Moodle
CVE-2020–25627, CVE-2020–14321, CVE-2020–25629, CVE-2019-11631
Do we really need to introduce what Moodle is....? 😅Okay...😂
Moodle is a popular open-source learning management system (LMS) used by many educational institutions around the world. It is a platform designed to support online learning and course management.
Carleton College (Yes, it's our school) uses Moodle as its primary LMS. Moodle is integrated into Carleton's teaching and learning infrastructure, and it is used by faculty to deliver course content and manage student assignments, quizzes, and grades.
According to the official Moodle website, as of 2021, there are over 190 million users in over 247 countries who use Moodle.
Which means...there are also millions and millions of desperate users, who really want to change their grades or checkout homework answers....🧐
Here's some info:
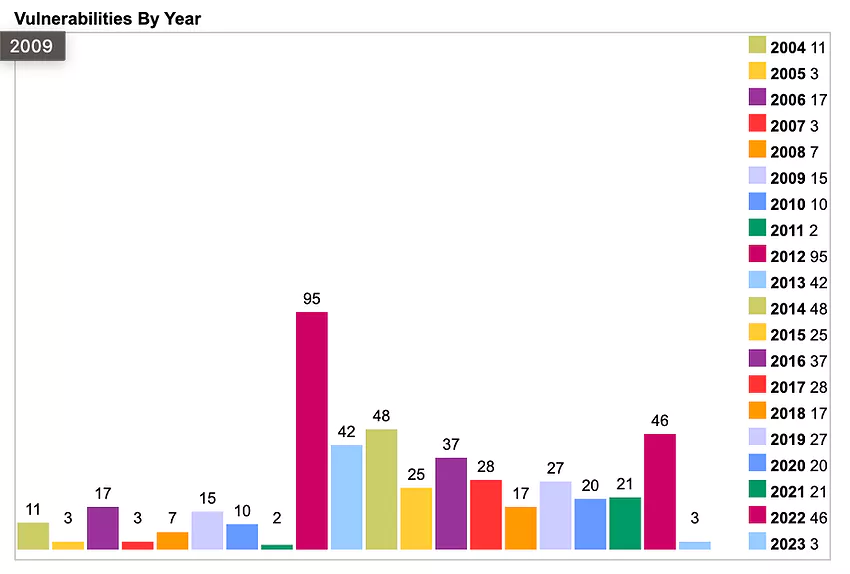
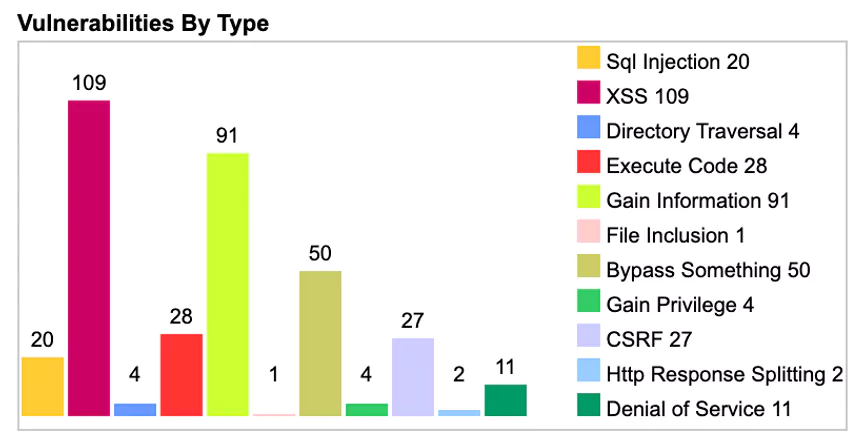 So Moodle is not a solid wall after all?
So Moodle is not a solid wall after all?
But seriously, don't get too excited 🙂.
In the video, 4 moodle vulnerbilities were introduced. Here we will provide brief introductions to all for of them.
1: ZIP File Repository_Ajax.php Code Injection
CVE-2019-11631
A vulnerability classified as critical was found in Moodle 3.6.3 . This vulnerability affects a code block of the file repository/repository_ajax.php?action=upload of the component ZIP File Handler.The manipulation with an certain input leads to a code injection vulnerability.
The vulnerbility allows an attacker to generate a plugin which can receive a malicious payload request and upload it to a server running Moodle, provided valid admin credentials are used. Metasploit Module
2: Teacher Privilege Escalation to RCE
CVE-2020–14321
CVE-2020-14321 is a privilege escalation vulnerability impacting multiple versions of Moodle. The vulnerability is found In Moodle before 3.9.1, 3.8.4, 3.7.7 and 3.5.13, and it could be exploited if you either have teacher credentials (don't know how likely that is) or a teacher cookie, as demonstrated in the video.The flaw in the privileges system allows a teacher to add themselves as a manager to their own class, and then add any other users, including someone with manager privileges on the system (not just the class).
A Metasploit module was observed in open source and a link to an exploit was shared. Additionally, a walk-through demo of an exploit was shared via YouTube. PoC Link Metasploit Module
3: Missing Authorization
CVE-2020-25629
A vulnerability was found in Moodle where users with "Log in as" capability in a course context (typically, course managers) may gain access to some site administration capabilities by "logging in as" a System manager.The flaw effects Moodle 3.9 to 3.9.1, 3.8 to 3.8.4, 3.7 to 3.7.7, 3.5 to 3.5.13 and earlier unsupported versions. This is fixed in 3.9.2, 3.8.5, 3.7.8 and 3.5.14.
A workaround prior to the applying the patches was removing the "Login as other users" capability from the manager role.
Once the attacker has executed the exploit, they can then gain elevated privileges on the Moodle site and perform various malicious activities, such as stealing user data, modifying or deleting data, and executing commands.
4: Stored XSS via moodlenetprofile parameter in user profile
CVE-2020-25627
Stored cross-site scripting (also known as second-order or persistent XSS) when an attacker is able to inject malicious code into the website or application, which is then stored in a database or other data store.In this case, when a teacher visits the affected student profile page, the malicious code is executed in their browser, which can allow the attacker to steal their sensitive information, such as passwords, cookies, or other personal data.
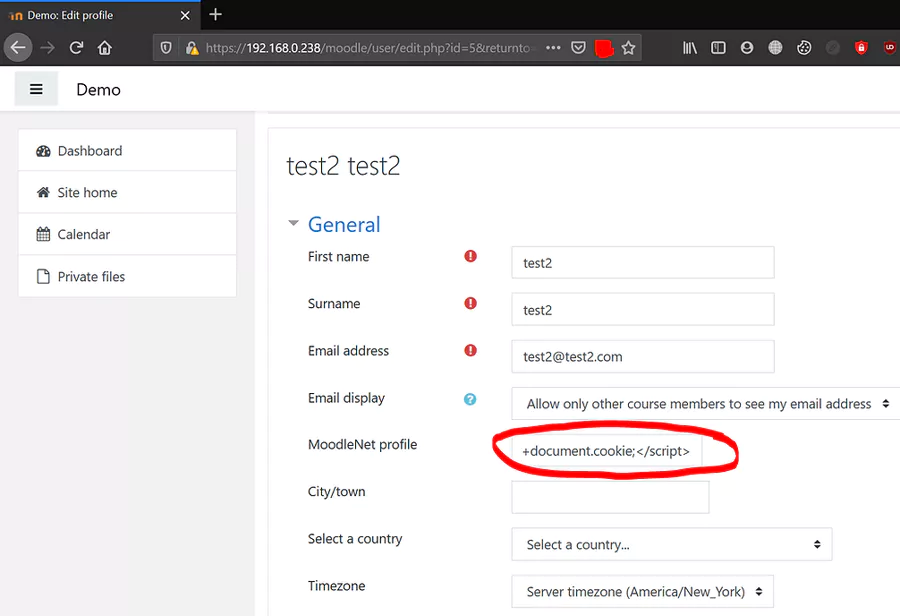 This vulnerability classified as problematic has been found in
Moodle up to 3.9.0/3.9.1
This vulnerability classified as problematic has been found in
Moodle up to 3.9.0/3.9.1
Note that CVE-2020-25627 and CVE-2020-14321 have to be chained together in order to gain access as a teacher user, escalate privileges to a manager user and install a malicious plugin resulting in remote command execution.
Cracking a hash obtained from the Moodle database allows SSH access to the system via password reuse. Privileges can then be escalated to root by installing a malicious package (which is possible due to sudo permissions and write access to the /etc/hosts file). PoC Link